TL;DR
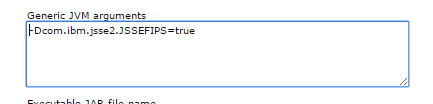
To enable CSIv2 for inbound and outbound launch the wsadmin tool with -lang jython and issue the following command:
AdminTask.configureCSIOutbound('[-transportLayer 'SSL-required']')
AdminTask.configureCSIInbound('[-transportLayer 'SSL-required' ]')
AdminConfig.save()
Using the console:
Set the inbound and outbound transports in the administrative console. Make sure that administrative security is enabled.
- WebSphere Application Server Version 7.0: Click . Change the transport type under the CSIv2 Transport Layer to SSL-Required.
Transport values:
TCP/IP SSL-required SSL-supported